
Four Bachelor of Science in Cybersecurity majors took first place in the Senior Design category of Design Expo 2022 for their project, “222: IoMT Device Security.” The students–Jacson Ott, Stu Kernstock, Trevor Hornsby, and Matthew Chau–are among the more than 1,000 students who participated in the event. Their winning project was sponsored by the Department of Applied Computing (AC) and advised by AC faculty member Guy Hembroff, Applied Computing. View the winning project, and all the Senior Design projects entered by College of Computing students, below. View the Enterprise projects entered in Design Expo 2022 here.
The annual Design Expo is Michigan Tech’s annual showcase for experiential, discovery-based learning. Each spring the event showcases the work of more than 1,000 students from Enterprise and Senior/Capstone Design programs. Student teams from all five Colleges–Business, Computing, Engineering, Forest Resources and Environmental Science, and Sciences and Arts–were represented. The 2022 Design Expo is generously supported by industry and university event sponsorship. View all Design Expo 2022 Senior Design entries here.
222: IoMT Device Security (Senior Design)

- Jacson Ott, Stu Kernstock, Trevor Hornsby, and Matthew Chau, Cybersecurity
- Advisor: Guy Hembroff, Applied Computing
- Sponsor: Department of Applied Computing
Our team researched the current security of Internet of Medical Things (IoMT) wearable devices. We have tested a wide selection of different smartwatches and accompanying smartphones for a number of different potential vulnerabilities. These include physical attacks, sniffing, man in the middle, dos, reverse application engineering, and more. The main purpose is to identify common weaknesses in security across this field, and to provide suggestions for mediation.
The goal of this project is to test the possibilities of security vulnerabilities between the connection of an Apple Watch and an iPhone. This is relevant because Apple devices are the most popular fitness tracking device on the market, and research shows that Bluetooth is vulnerable to certain attacks. This is especially true with its counterpart Bluetooth Low Energy, which has recently been tested for its security. We are currently in our second phase, where we are testing connections with a multitude of tools.
204: Bluetooth Attacks on Medical Wearables (Senior Design)
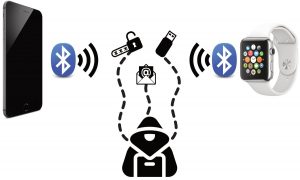
- Team members: Destiny Michaels, Cam Kern, Joseph Horne, Byron Langerman, Computer Network and System Administration
- Advisor: Tim Van Wagner, Applied Computing
- Sponsor: Department of Applied Computing
The goal of this project is to test the possibilities of security vulnerabilities between the connection of an Apple Watch and an iPhone. This is relevant because Apple devices are the most popular fitness tracking device on the market, and research shows that Bluetooth is vulnerable to certain attacks. This is especially true with its counterpart Bluetooth Low Energy, which has recently been tested for its security. We are currently in our second phase, where we are testing connections with a multitude of tools.
212: Drone-Based Crack Detection System (Senior Design)

- Eric Batz and Jason Sherred, Electrical Engineering Technology
- Advisor: Ashraf Saleem, Applied Computing
- Department of Applied Computing
The goal of the Drone-Based Crack Detection System is to reduce the cost and risk to workers who are inspecting areas that may be unsafe. With the use of Intel RealSense, a Raspberry Pi, and Artificial Intelligence (AI), the drone will be able to detect and label cracks in infrastructure. The drone will send live video feedback to the user with a screenshot to save. This data collected will be used to train the AI continuously.
216: Emergency Situation Solar Generator (Senior Design)
- Team members: Alexander Rogers, Josh Kiefer, and Daren Giuchin, Electrical Engineering Technology
- Advisor: Ashraf Saleem, Applied Computing
- Sponsor: Department of Applied Computing
Our team was tasked with developing an affordable power source that can be resupplied via renewable solar power. The main purpose of this generator is to be deployed and used for communications and other low-voltage systems following extreme weather conditions that disable local power and disrupt the local energy supply chain.
219: High Availability Cybersecurity Kit (Senior Design)

- Team members: Jerod Warren, Brad Gipson, and Brandon Lopez, Computer Network and System Administration
- Advisor: Yu Cai, Applied Computing
- Sponsor: Department of Applied Computing
Our team developed the High Availability Cybersecurity Kit (H.A.C.K.), a low-cost cybersecurity training kit for middle school and high school students. H.A.C.K. will introduce the concepts of networking, Linux, Raspberry Pi, password cracking, wireless attacks, and much more. Modules with tutorials will lead students through the activities with a focus on experimentation and exploration, hopefully lighting a spark of curiosity that could lead into a career in cybersecurity.
223: IoT Course Development for CNSA Curriculum (Senior Design)

- Team members: Olivia Uzosike and Kate MacQuarrie-Klender, Cybersecurity and Brandon Cox, Computer Network and System Administration
- Advisor: Sidike Paheding, Applied Computing
- Sponsor: Department of Applied Computing
The goal of this project is to implement some topic that is not covered sufficiently enough within the CNSA curriculum. We first determined that topics surrounding the Internet of Things would be a sufficient topic. We then created ten labs, ten modules, homework, and a final exam for topics surrounding IoT, including data administration, IoT security and protocols, history, modern and future use of IoT, cloud and fog computing, analytics, and implementation of IoT. Upon completion of the modules we began a lab-testing phase to finalize our project. Currently, we are using IoT-based hardware including nest cameras, raspberry pi pico, and raspberry pi, to test security and implementation based IoT techniques.
240: Project Athena (Senior Design)

- Team members: Fiona Chow, Rylee Gorman, Macy Pawielski, Chris Arbuckle, and Brendon Cook, Management Information Systems; Jessica Brown, Computer Science
- Advisor: Jeffrey Wall, College of Business and Economics
- Sponsor: Needlestack
The goal of this project is to help with the creation of a learning management system (LMS). Our team is split into two subteams–research and technical. The research subteam’s main tasks are market and user research through customer discovery methods such as conducting interviews with various end users. The technical subteam is using Adobe XD to design an automated grading pipeline. The subteams will come together to perform usability testing on the prototype design and collect user feedback to share with the client.
256: WarDriving IoT (Senior Design)

- Team members: Darren Hutchinson, Matthew Hoying, Lucas Runkel, Seth Hessbrook, and Devin Schultz, Computer Network and System Administration, and Eli Brockert, Cybersecurity
- Advisor: Tim Van Wagner, Applied Computing
- Sponsor: Michigan Tech Department of Applied Computing
Our project is composed of two focused subgroups: Offensive Red Team and Defensive Blue Team. The goal for Red Team is to utilize IoT hardware and complimentary open-source software to perform penetration testing on a network. Phases of Red Team’s project will include detection, intrusion, and attacking devices on a network while keeping cost to a minimum. The goal for Blue Team is to utilize IoT hardware and software to defend a network. Blue Team’s focus is set up in three phases: basic network setup, advanced user setup, and network lockdown. Each phase will incorporate different levels of configuration and introduce new IoT devices and software to help monitor and defend against Red Team’s attack vectors.






